Announce upcoming external penetration test
 You will get to know about scripting and input validation flaws, AJAX, and security issues related to AJAX. If you are the administrator of this website note that your access has been limited because you broke one of the Wordfence advanced blocking rules. Fuzz, port scan, or run vulnerability assessment tools against your own Azure Virtual Machines. IT - Pen Test Review Q 8a, Automated Integrated Regulatory Examination System AIRES IT Exam Questionnaires, version A Did the penetration test work plan include infrared systems testing? Microsoft offers bug bounty awards and recognition for many types of security issues. We're happy to answer your specific questions.
You will get to know about scripting and input validation flaws, AJAX, and security issues related to AJAX. If you are the administrator of this website note that your access has been limited because you broke one of the Wordfence advanced blocking rules. Fuzz, port scan, or run vulnerability assessment tools against your own Azure Virtual Machines. IT - Pen Test Review Q 8a, Automated Integrated Regulatory Examination System AIRES IT Exam Questionnaires, version A Did the penetration test work plan include infrared systems testing? Microsoft offers bug bounty awards and recognition for many types of security issues. We're happy to answer your specific questions.


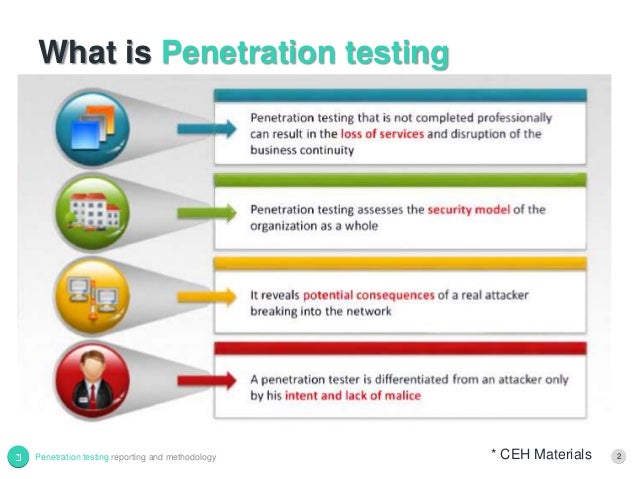
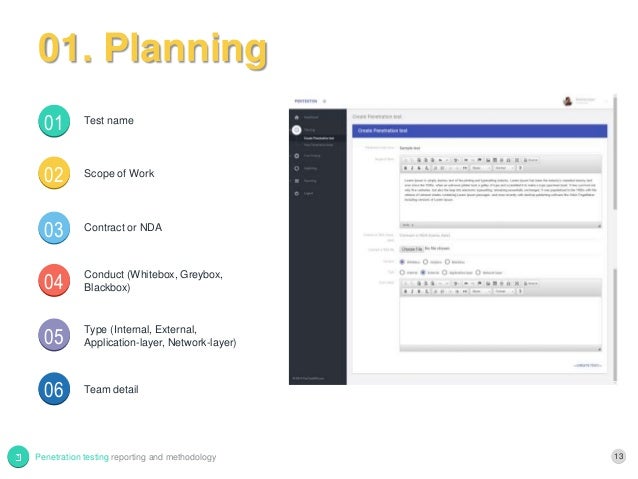
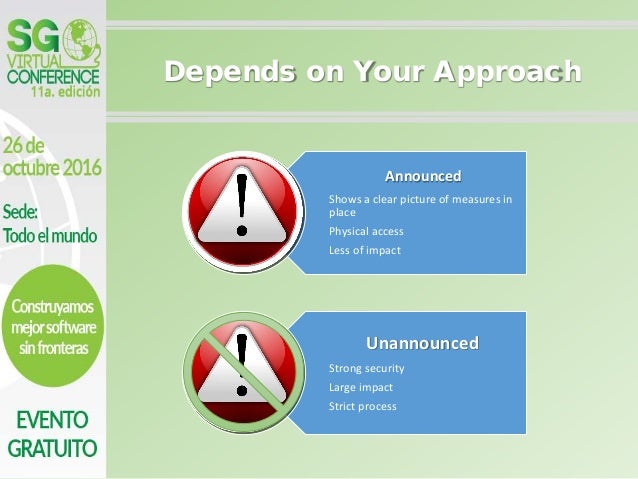
5 Must-Have Network Penetration Testing Strategies
 Even worse, they may cause you to miss critical entry point vulnerabilities that show up in the lower severities. Double blind testing Double blind testing takes the blind test and carries it a step further. Get all users in the domain "opsdc" PS C: Traditionally, organizations have sought to prevent breaches by installing and maintaining layers of defensive security mechanisms, including user access controls, cryptography, IPS, IDS and firewalls. Penetration testing also called pen testing is the practice of testing a computer system, network or Web application to find vulnerabilities that an attacker could exploit. PowerView uses LDAP queries which ATA does not care about currently for enumeration. Thus, it is becoming more important that these applications are highly available.
Even worse, they may cause you to miss critical entry point vulnerabilities that show up in the lower severities. Double blind testing Double blind testing takes the blind test and carries it a step further. Get all users in the domain "opsdc" PS C: Traditionally, organizations have sought to prevent breaches by installing and maintaining layers of defensive security mechanisms, including user access controls, cryptography, IPS, IDS and firewalls. Penetration testing also called pen testing is the practice of testing a computer system, network or Web application to find vulnerabilities that an attacker could exploit. PowerView uses LDAP queries which ATA does not care about currently for enumeration. Thus, it is becoming more important that these applications are highly available.
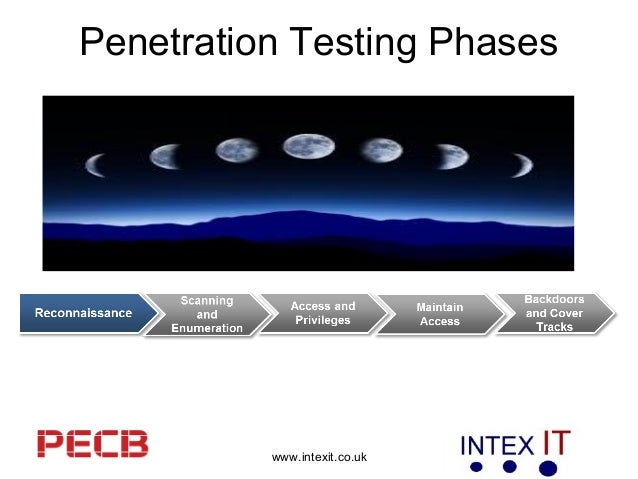
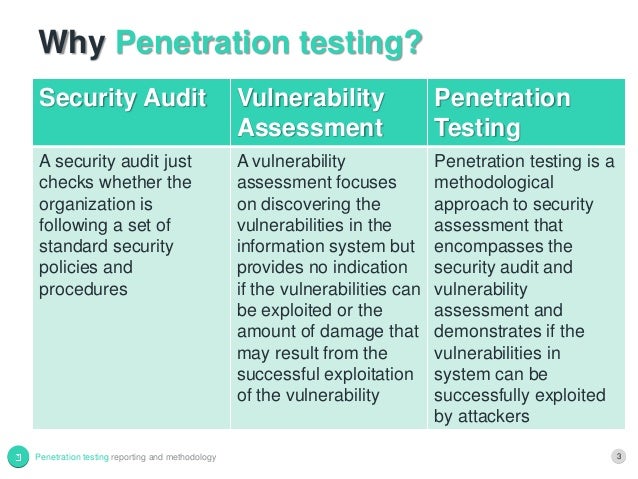
What is pen test (penetration testing)? - Definition from MY-SOCCER.CLUB
People are using different operating systems and CPU architectures such as 32 or 64 bit. The objective is to find out if an outside attacker can get in and how far they can get in once they've gained access. Since we already have a list of users, let's try brute-force attack against all the users in the domain. Penetration Testing vs Vulnerability Assessment This email address is being protected from spambots.


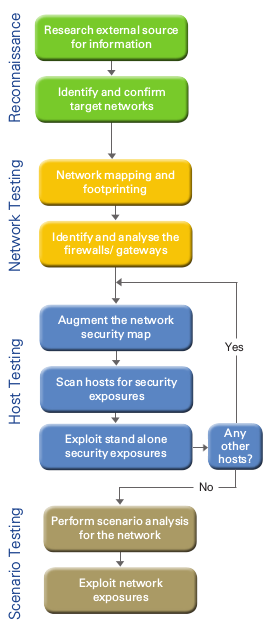


Your access to this site has been limited

Description: In a paper, Ware referred to the military's remotely accessible time-sharing systems, warning that "Deliberate attempts to penetrate such computer systems must be anticipated. We will follow a simple "attack chain" where we begin with a normal domain user privileges and then work our way up to domain dominance. Find an exploitable vulnerability. Vulnerability assessments conducted with domain administrator credentials provide specific visibility into the effectiveness of your patch management program particularly with third party applications. Penetration Testing vs Vulnerability Assessment This email address is being protected from spambots.
Views: 5717
Date: 23.10.2017
Favorited: 5















.gif)







.jpg)













good smile