Assessment penetration test vulnerability
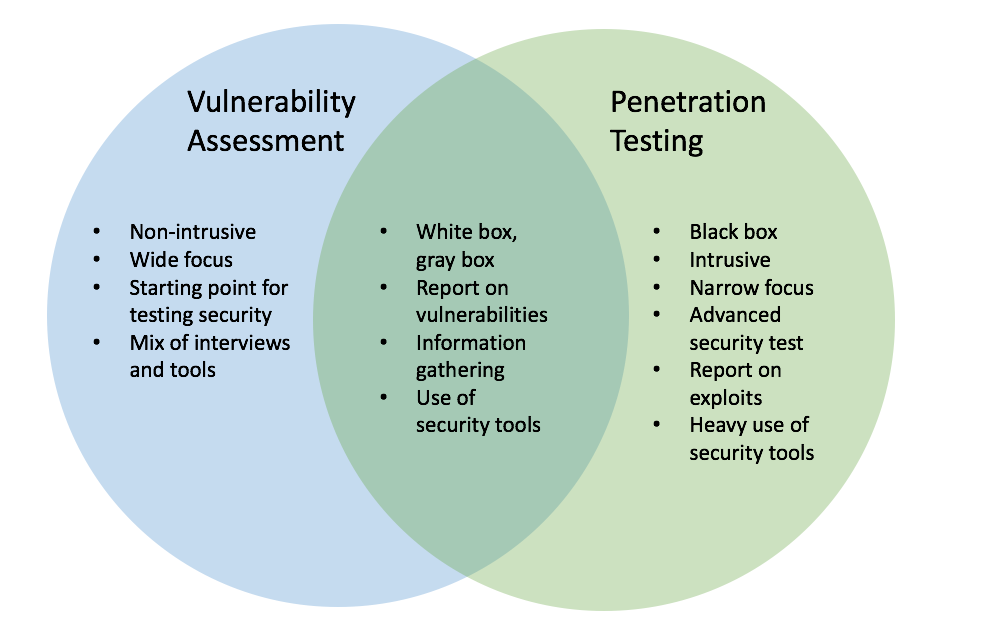
 The VA process gives a horizontal map into the security position of the network and the application, while the PT process does a vertical deep dive into the findings. Usually requested by customers who already know they have issues, and need help getting started. Vodafone deploys open source to reduce vendor lock-in June 9, Stepping into the world of Linux Containers LXC. Everything you need to know about Arduino. The time and effort to conduct the penetration tests on the system should be estimated.
The VA process gives a horizontal map into the security position of the network and the application, while the PT process does a vertical deep dive into the findings. Usually requested by customers who already know they have issues, and need help getting started. Vodafone deploys open source to reduce vendor lock-in June 9, Stepping into the world of Linux Containers LXC. Everything you need to know about Arduino. The time and effort to conduct the penetration tests on the system should be estimated.




Penetration Testing & Vulnerability Assessment
 What is a Vulnerability Assessment? A vulnerability assessment answers the question: These scans can be a perfunctory as a port scan, or a scan for PCI compliance or the OWASP top ten vulnerabilities. Application Attack Types ARP Spoofing Botnet Cache Poisoning Computer Worm Keylogger LDAP Injection Malware Man in the Middle Attack Rootkit Spoofing Attack Spyware. Where a vulnerability scan can be automated, a penetration test requires various levels of expertise within your scope of systems. Vulnerability Assessment and Penetration Testing VAPT are two types of vulnerability testing. The customer already knows they have issues and simply need help identifying and prioritizing them.
What is a Vulnerability Assessment? A vulnerability assessment answers the question: These scans can be a perfunctory as a port scan, or a scan for PCI compliance or the OWASP top ten vulnerabilities. Application Attack Types ARP Spoofing Botnet Cache Poisoning Computer Worm Keylogger LDAP Injection Malware Man in the Middle Attack Rootkit Spoofing Attack Spyware. Where a vulnerability scan can be automated, a penetration test requires various levels of expertise within your scope of systems. Vulnerability Assessment and Penetration Testing VAPT are two types of vulnerability testing. The customer already knows they have issues and simply need help identifying and prioritizing them.
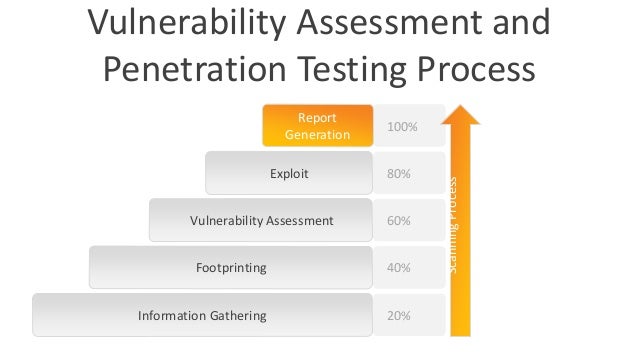
Vulnerability Assessment & Penetration Testing | Veracode
Some common and decent vulnerability scanners are: Newsletter Every Sunday I put out a list of the most interesting stories in infosec, technology, and humans. Vulnerability Assessments You are here: Veracode's binary scanning approach produces more accurate testing results using methodologies developed and continually refined by a team of world-class experts.




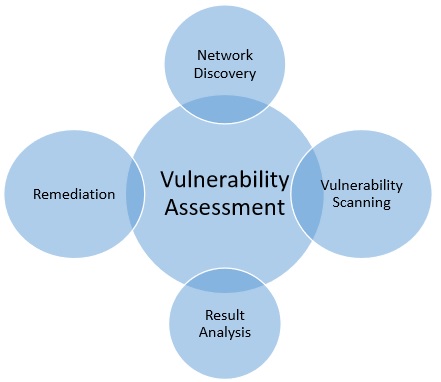
VULNERABILITY ASSESSMENT AND PENETRATION TESTING

Description: Now, penetration testing is a little different. In short, Penetration Testing and Vulnerability Assessments perform two different tasks, usually with different results, within the same area of focus. FFIEC; GLBA; PCI DSS. Many organizations deploy standard builds to support key Internet accessible services or environments.
Views: 5368
Date: 24.11.2016
Favorited: 5











.jpg)


.gif)





















0