Penetration and vulnerability testing
 Summary There are many views on what constitutes a Vulnerability Assessment versus a Penetration Test. Another mistake people make when discussing vulnerability assessments vs. We already have an aptly named I might add security test for compiling a complete list of vulnerabilities, i. The technique is used to estimate how susceptible the network is to different vulnerabilities. The more issues identified the better, so naturally a white box approach should be embraced when possible. Next Page Generally, these two terms, i. Both the methods have different functionality and approach, so it depends upon the security position of the respective system.
Summary There are many views on what constitutes a Vulnerability Assessment versus a Penetration Test. Another mistake people make when discussing vulnerability assessments vs. We already have an aptly named I might add security test for compiling a complete list of vulnerabilities, i. The technique is used to estimate how susceptible the network is to different vulnerabilities. The more issues identified the better, so naturally a white box approach should be embraced when possible. Next Page Generally, these two terms, i. Both the methods have different functionality and approach, so it depends upon the security position of the respective system.




VULNERABILITY ASSESSMENT AND PENETRATION TESTING
 Penetration testing can operate at the application- or network-level or be specific to a function, department, or number of assets. The Question of Exploitation Another mistake people make when discussing vulnerability assessments vs. Vulnerability assessment tools discover which vulnerabilities are present, but they do not differentiate between flaws that can be exploited to cause damage and those that cannot. Language is important, and we have two terms for a reason. With that in mind, I'd like to try to clarify the distinctions between vulnerability assessments and pen tests and hopefully eliminate some of the confusion. Because of its cost and its higher-than-average chance of causing outages, penetration testing is often conducted once a year.
Penetration testing can operate at the application- or network-level or be specific to a function, department, or number of assets. The Question of Exploitation Another mistake people make when discussing vulnerability assessments vs. Vulnerability assessment tools discover which vulnerabilities are present, but they do not differentiate between flaws that can be exploited to cause damage and those that cannot. Language is important, and we have two terms for a reason. With that in mind, I'd like to try to clarify the distinctions between vulnerability assessments and pen tests and hopefully eliminate some of the confusion. Because of its cost and its higher-than-average chance of causing outages, penetration testing is often conducted once a year.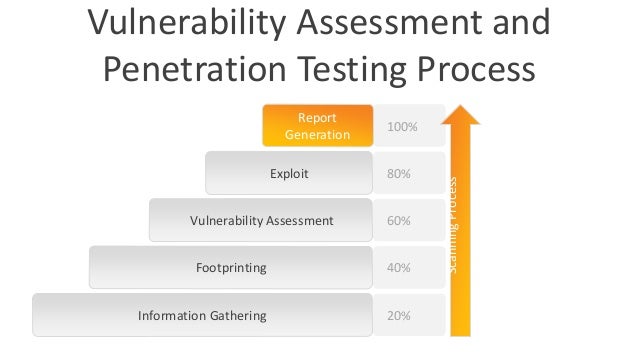

Penetration Testing & Vulnerability Assessment
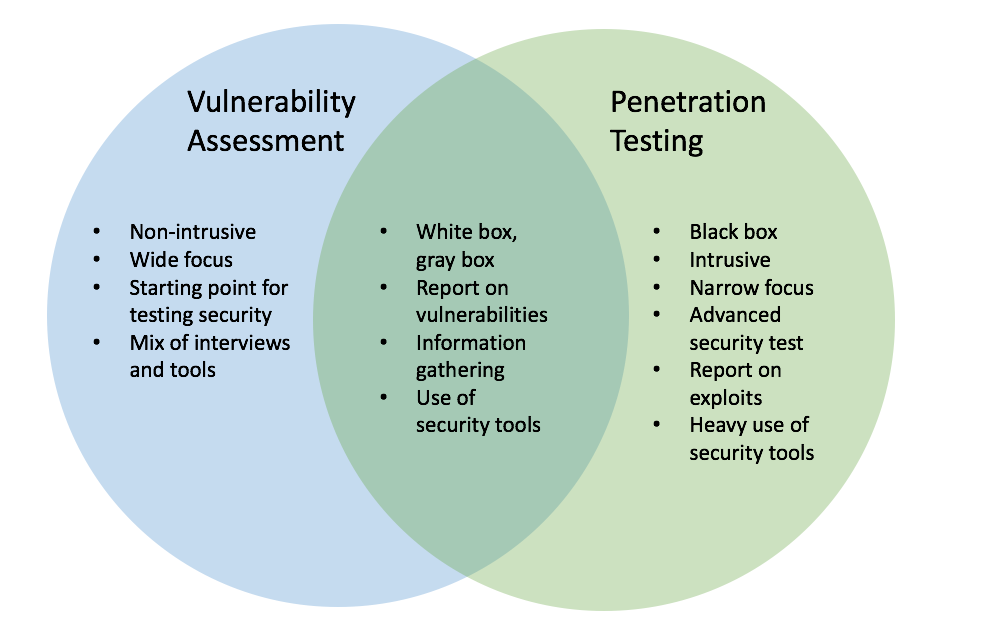
Penetration Tests are designed to achieve a specific, attacker-simulated goal and should be requested by customers who are already at their desired security posture. Get started with Tenable. The basic narrative is:. Penetration testing exploits vulnerabilities in your system architecture while vulnerability scanning or assessment checks for known vulnerabilities and generates a report on risk exposure. When communicating your event, please be sure to provide details on the event including:



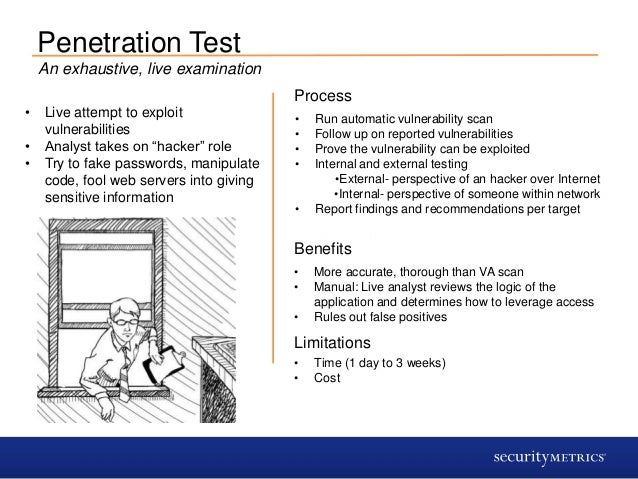


The Difference between Vulnerability Scanning and Penetration Testing

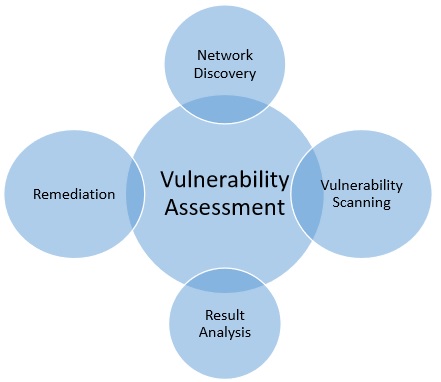
Description: It is an in-depth evaluation of your information security posture, indicating weaknesses as well as providing the appropriate mitigation procedures required to either eliminate those weaknesses or reduce them to an acceptable level of risk. Both are valuable tools that can benefit any information security program and they are both integral components of a Threat and Vulnerability Management process. Request Penetration Test Authorization. Please email us directly at aws-security-simulated-event amazon.
Views: 4767
Date: 17.01.2018
Favorited: 5




































User Comments
Post a comment
Comment: