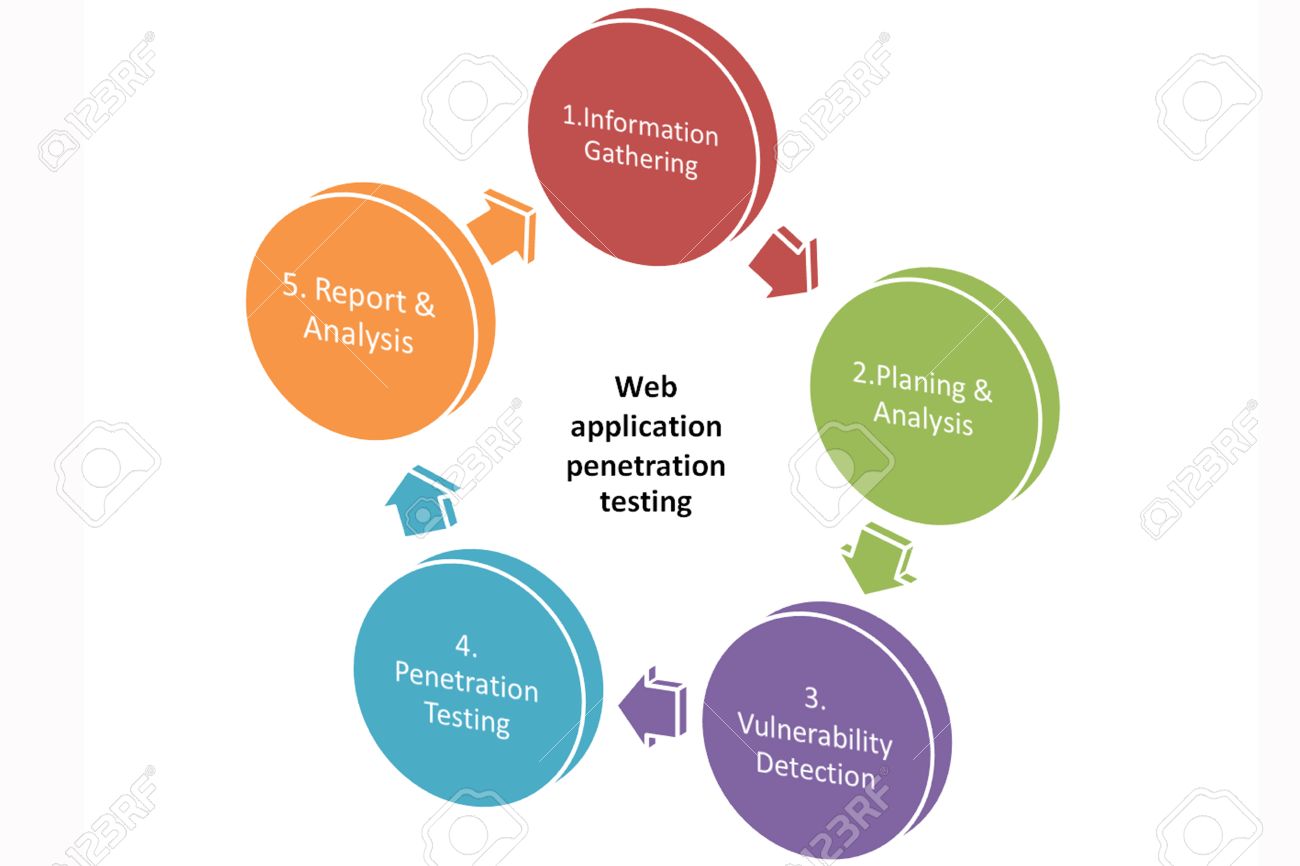
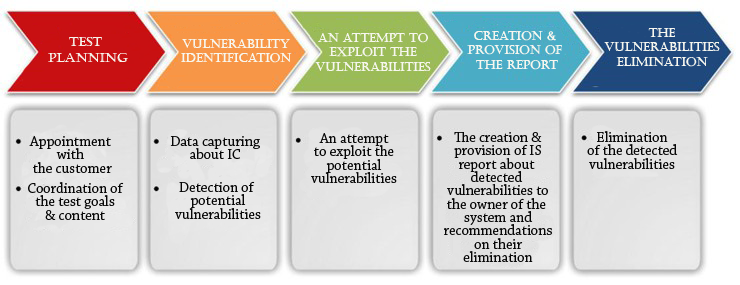
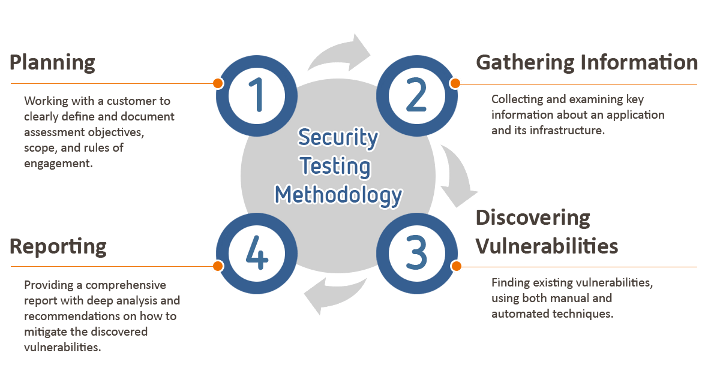
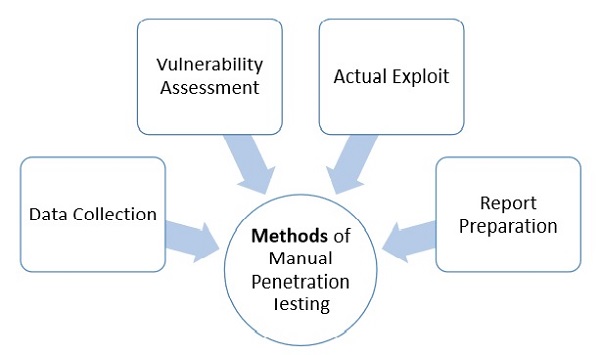
Stages of penetration testing
 Tools What links here Related changes Special pages Printable version Permanent link Page information. LOG IN TO COMMENT. Phase 5 — Covering Tracks Take the necessary steps to hide the intrusion and possible controls left behind for future visits. In addition to the defensive steps described above, security managers should make every effort to ensure end-user devices and servers are not easily accessible by unauthenticated users. Limitations of Penetration Testing The Phases of an Attack Security Audits Security Assessments, Vulnerabilty Assessments vs Penetration Testing Additional Penetration Test Types Types of Penetration Tests Why Penetration Testing? Privacy Policy Cookies Ad Choice Terms of Use Mobile User Agreement.
Tools What links here Related changes Special pages Printable version Permanent link Page information. LOG IN TO COMMENT. Phase 5 — Covering Tracks Take the necessary steps to hide the intrusion and possible controls left behind for future visits. In addition to the defensive steps described above, security managers should make every effort to ensure end-user devices and servers are not easily accessible by unauthenticated users. Limitations of Penetration Testing The Phases of an Attack Security Audits Security Assessments, Vulnerabilty Assessments vs Penetration Testing Additional Penetration Test Types Types of Penetration Tests Why Penetration Testing? Privacy Policy Cookies Ad Choice Terms of Use Mobile User Agreement..gif)


Main Page
 Together with the jQuery JavaScript framework, this triumvirate forms a symbiosis of technology and user-friendliness. INVENSITY supports you to market your technological strengths and capabilities. The most important thing to remember is that while permission may have been granted by the client, they do not speak for their third party providers. However, there are no clear system requirements for such mobile PV systems. Every organization needs skilled information security personnel who can find vulnerabilities and mitigate their effects, and this entire course is specially designed to get you ready for that role. The aim of this section of the PTES is to present and explain the tools and techniques available which aid in a successful pre-engagement step of a penetration test.
Together with the jQuery JavaScript framework, this triumvirate forms a symbiosis of technology and user-friendliness. INVENSITY supports you to market your technological strengths and capabilities. The most important thing to remember is that while permission may have been granted by the client, they do not speak for their third party providers. However, there are no clear system requirements for such mobile PV systems. Every organization needs skilled information security personnel who can find vulnerabilities and mitigate their effects, and this entire course is specially designed to get you ready for that role. The aim of this section of the PTES is to present and explain the tools and techniques available which aid in a successful pre-engagement step of a penetration test.

Oksana. Age: 28. hot&classy sara, companion in moscow! I'm a so lovely girl with big boobs who waiting you for make reality all your dreams!
Security testing - Wikipedia
Many test cases are covered in the pen testing. In , he joined the business development department as an associate business consultant, combining his technical background with knowledge in economics and project management. You want to boost growth in your company by innovation? A Firewall can be a software or hardware to block unauthorized access to system. It discusses how the tools interrelate with each other in an overall testing process.






Security testing

Description: Search AWS Hone your AWS expertise to adapt in an AppDev world New and experienced IT pros alike struggle to gain the AWS know-how to stay relevant in an evolving space. To that end, below is a list of things that you can benchmark while testing. That approach, however, creates management woes. Network Penetration Testing and Ethical Hacking SANS Phoenix-Mesa Mesa, AZ Adrien de Beaupre. There are a number of different justifications for this reasoning.
Views: 4259
Date: 09.05.2017
Favorited: 5


































User Comments
Post a comment
Comment: